セ・パ交流戦も終わり、梅雨が明ければいよいよ夏ですね!
今年のゴールデンウィークは九州旅行に行ってまいりました。
五島列島なんかも行ってきまして、大変有意義なお休みとなりました。
写真は佐賀県の浜野浦の棚田展望台という場所で、墨絵のような陰影が美しいですね!
えーワタクシ、専門はネットワーク関連ですのでたまにはネットワークネタを書いてみたいと思います。
IP-VPNやVPLS、現在ホットなEVPN環境を作ってみる、、、、とかやってみたらカッコいいし社内のメンツが保てる、、と思いましたが、ある程度気合が必要なのと、ややこしくて説明が長くなりそうなので、もっと実用的なやつにします。
社内で色々なお客様案件の作業を行っていますと、検証環境や擬似環境が欲しくなる場合があります。
IPアドレスを検証用に実際とは異なるものを使用するのはなく、なるべくその案件の実IPを使用したいものです。
そこで大体課題となるのがIPアドレス帯のバッティングです。正確に言おうとしますと、「独立したアドレス管理空間相互通信時のルーティングにおけるアドレス競合」とでも言いましょうか。
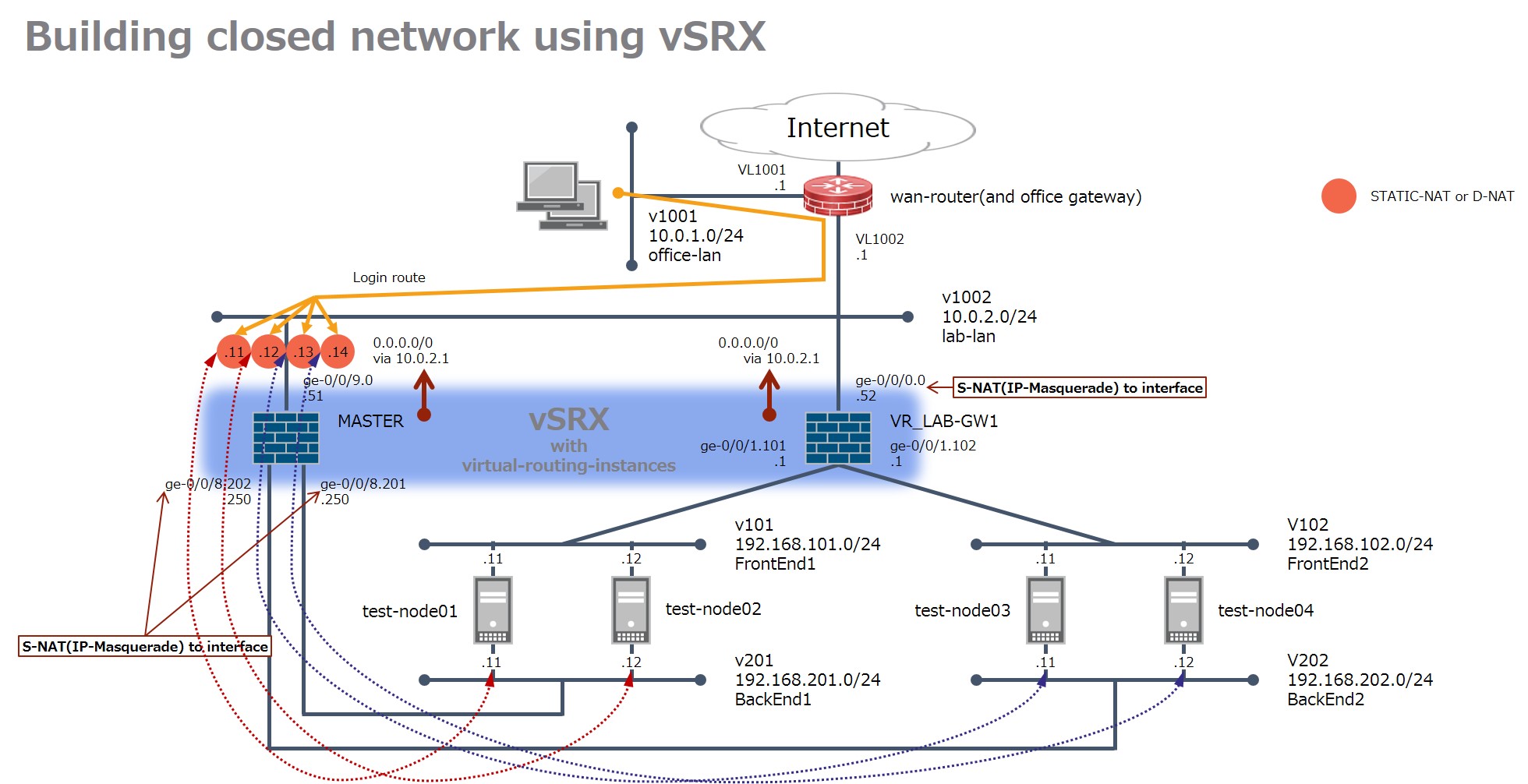
ここではvSRXを用いて一般的なサーバーファーム構成(フロントエンド/バックエンド)の検証・擬似用ネットワークを、社内LANとは分離してサクッと作るテンプレート的な構成例を紹介します。
vSRXは以下のJuniper社のサイトからダウンロードできます。※現在は削除しました
※vSRXをダウンロードするにはJuniperのアカウントを作成する必要があります。アカウントはGuestで登録すればダウンロードできます。
仮想環境にてovaファイルから簡単にデプロイすることができます。(ここは省略)
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 |
set version 12.1X47-D20.7 set system host-name test-login-gw set system time-zone Asia/Tokyo set system ports console log-out-on-disconnect set system root-authentication encrypted-password <暗号化されたパスワード(for root)> set system name-server <dns-primary-IP> set system name-server <dns-secondary-IP> set system login user user uid 2001 set system login user user class super-user set system login user user authentication encrypted-password <暗号化されたパスワード(for user)> set system services ssh set system services telnet set system ntp server <ntp-server-IP> version 4 set interfaces ge-0/0/0 unit 0 description LAB-GW1_EXTERNAL set interfaces ge-0/0/0 unit 0 family inet address 10.0.2.52/24 set interfaces ge-0/0/1 vlan-tagging set interfaces ge-0/0/1 unit 101 description FrontEnd1 set interfaces ge-0/0/1 unit 101 vlan-id 101 set interfaces ge-0/0/1 unit 101 family inet address 192.168.101.1/24 set interfaces ge-0/0/1 unit 102 description FrontEnd2 set interfaces ge-0/0/1 unit 102 vlan-id 102 set interfaces ge-0/0/1 unit 102 family inet address 192.168.102.1/24 set interfaces ge-0/0/8 vlan-tagging set interfaces ge-0/0/8 unit 201 description BackEnd1_LOGIN set interfaces ge-0/0/8 unit 201 vlan-id 201 set interfaces ge-0/0/8 unit 201 family inet address 192.168.201.250/24 set interfaces ge-0/0/8 unit 202 description BackEnd2_LOGIN set interfaces ge-0/0/8 unit 202 vlan-id 202 set interfaces ge-0/0/8 unit 202 family inet address 192.168.202.250/24 set interfaces ge-0/0/9 unit 0 description MASTER-LOGIN_EXTERNAL set interfaces ge-0/0/9 unit 0 family inet address 10.0.2.51/24 set routing-options static route 0.0.0.0/0 next-hop 10.0.2.1 set security nat source rule-set SRC-NAT-R-SET_LOGIN from interface ge-0/0/9.0 set security nat source rule-set SRC-NAT-R-SET_LOGIN to routing-instance default set security nat source rule-set SRC-NAT-R-SET_LOGIN rule SRC-NAT-R_LOGIN match source-address 0.0.0.0/0 set security nat source rule-set SRC-NAT-R-SET_LOGIN rule SRC-NAT-R_LOGIN then source-nat interface set security nat source rule-set SRC-NAT-R-SET_LAB-GW1 from routing-instance VR_LAB-GW1 set security nat source rule-set SRC-NAT-R-SET_LAB-GW1 to interface ge-0/0/0.0 set security nat source rule-set SRC-NAT-R-SET_LAB-GW1 rule SRC-NAT-R_LAB-GW1-INET match source-address 0.0.0.0/0 set security nat source rule-set SRC-NAT-R-SET_LAB-GW1 rule SRC-NAT-R_LAB-GW1-INET then source-nat interface ~~~~以下は構成に応じて選択 ~~pattern-1 (static-nat) set security nat static rule-set ST-NAT-R-SET_LOGIN from interface ge-0/0/9.0 set security nat static rule-set ST-NAT-R-SET_LOGIN rule ST-NAT-R_lab-test-node01 match destination-address 10.0.2.11/32 set security nat static rule-set ST-NAT-R-SET_LOGIN rule ST-NAT-R_lab-test-node01 then static-nat prefix 192.168.201.11/32 set security nat static rule-set ST-NAT-R-SET_LOGIN rule ST-NAT-R_lab-test-node02 match destination-address 10.0.2.12/32 set security nat static rule-set ST-NAT-R-SET_LOGIN rule ST-NAT-R_lab-test-node02 then static-nat prefix 192.168.201.12/32 set security nat static rule-set ST-NAT-R-SET_LOGIN rule ST-NAT-R_lab-test-node03 match destination-address 10.0.2.13/32 set security nat static rule-set ST-NAT-R-SET_LOGIN rule ST-NAT-R_lab-test-node03 then static-nat prefix 192.168.202.11/32 set security nat static rule-set ST-NAT-R-SET_LOGIN rule ST-NAT-R_lab-test-node04 match destination-address 10.0.2.14/32 set security nat static rule-set ST-NAT-R-SET_LOGIN rule ST-NAT-R_lab-test-node04 then static-nat prefix 192.168.202.12/32 ~~pattern-2 (destination-nat) set security nat destination pool DST-NAT-P_lab-test-node01 address 192.168.201.11/32 set security nat destination pool DST-NAT-P_lab-test-node02 address 192.168.201.12/32 set security nat destination pool DST-NAT-P_lab-test-node03 address 192.168.202.11/32 set security nat destination pool DST-NAT-P_lab-test-node04 address 192.168.202.12/32 set security nat destination rule-set DST-NAT-R-SET_LOGIN from interface ge-0/0/9.0 set security nat destination rule-set DST-NAT-R-SET_LOGIN rule DST-NAT-R_lab-test-node01 match destination-address 10.0.2.11/32 set security nat destination rule-set DST-NAT-R-SET_LOGIN rule DST-NAT-R_lab-test-node01 then destination-nat pool DST-NAT-P_lab-test-node01 set security nat destination rule-set DST-NAT-R-SET_LOGIN rule DST-NAT-R_lab-test-node02 match destination-address 10.0.2.12/32 set security nat destination rule-set DST-NAT-R-SET_LOGIN rule DST-NAT-R_lab-test-node02 then destination-nat pool DST-NAT-P_lab-test-node02 set security nat destination rule-set DST-NAT-R-SET_LOGIN rule DST-NAT-R_lab-test-node03 match destination-address 10.0.2.13/32 set security nat destination rule-set DST-NAT-R-SET_LOGIN rule DST-NAT-R_lab-test-node03 then destination-nat pool DST-NAT-P_lab-test-node03 set security nat destination rule-set DST-NAT-R-SET_LOGIN rule DST-NAT-R_lab-test-node04 match destination-address 10.0.2.14/32 set security nat destination rule-set DST-NAT-R-SET_LOGIN rule DST-NAT-R_lab-test-node04 then destination-nat pool DST-NAT-P_lab-test-node04 ~~~~ set security nat proxy-arp interface ge-0/0/9.0 address 10.0.2.11/32 to 10.0.2.14/32 set security policies default-policy permit-all set security zones security-zone Z_MASTER-LOGIN host-inbound-traffic system-services all set security zones security-zone Z_MASTER-LOGIN host-inbound-traffic protocols all set security zones security-zone Z_MASTER-LOGIN interfaces ge-0/0/8.201 set security zones security-zone Z_MASTER-LOGIN interfaces ge-0/0/8.202 set security zones security-zone Z_MASTER-LOGIN interfaces ge-0/0/9.0 set security zones security-zone Z_LAB-GW1 host-inbound-traffic system-services all set security zones security-zone Z_LAB-GW1 host-inbound-traffic protocols all set security zones security-zone Z_LAB-GW1 interfaces ge-0/0/0.0 set security zones security-zone Z_LAB-GW1 interfaces ge-0/0/1.101 set security zones security-zone Z_LAB-GW1 interfaces ge-0/0/1.102 set routing-instances VR_LAB-GW1 instance-type virtual-router set routing-instances VR_LAB-GW1 interface ge-0/0/0.0 set routing-instances VR_LAB-GW1 interface ge-0/0/1.101 set routing-instances VR_LAB-GW1 interface ge-0/0/1.102 set routing-instances VR_LAB-GW1 routing-options static route 0.0.0.0/0 next-hop 10.0.2.1 |
いかがでしたでしょうか。これで自由にIPアドレスを使用した検証環境を構築できますね!